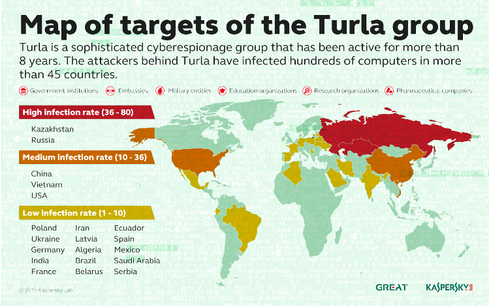
Turla’s activities were exposed last year; the Russian-speaking gang has carried out espionage campaigns against more than 500 victims in 45 countries. Named after the malicious software it uses, Turla is best known for targeting government agencies, embassies, military, pharmaceutical, and research organizations in the U.S., Kazakhstan, Russia, Vietnam, and China for eight years to gain political and strategic intelligence through exceptional methods, said Stefan Tanase, senior security researcher at Kaspersky Lab.
Turla has been compared by some with another Russian hacker group believed to be behind the hacking of the State Department, White House and Pentagon earlier this year. The attack on Pentagon included 4,000 military and civilian personnel working for the Joint Chiefs of Staff, and the network had to be shut down for two weeks in July. Speaking to The Washington Post about the satellite hackers, Stefan Tanase said “For us, it was very surprising. This is the first group that we believe has done it. It allows you to achieve a much greater level of anonymity.” Dmitri Alperovitch, co-founder and chief technology officer of CrowdStrike, an Irvine, California-based cybersecurity technology firm said that the Turla malware was created by a “sophisticated Russian-government-affiliated” hacker group that “we call Venomous Bear.” According to Finland, its Foreign Ministry computer systems had been hit by a Turla attack last year but no detailed information was provided about it. Kaspersky researchers wrote in a report that it’s use of hijacked downstream-only links is a cheap ($1,000 a year to maintain) and very easy means of moving malware and communicating with compromised machines. Although slow, those connections are a sign for hackers, as links are not encoded and fully developed for abuse. Turla targets the victim by planting malicious software on the website that it frequently visits and obtains sensitive data. Turla can gain control of the user’s computer as soon as the target opens the site. The hacker instructs the infected computer to send the stolen data to the Internet address of an innocent satellite user online who is using internet service provided by the satellite company. Turla then seizes control of the the stream of data that is being sent down from the satellite to the victim’s computer by spoofing the user’s internet address. The data is sent to a command server controlled by Turla by hiding it’s location, as it can be anywhere in the range of the satellite beam, which can be thousands of miles. It most often uses satellite internet connections in Middle Eastern and African countries to avoid the scrutiny of researchers and law enforcement. “[This technique] essentially makes it impossible for someone to shut down or see their command servers,” Tanase said. “No matter how many levels of proxies you use to hide your server, investigators who are persistent enough can reach the final IP address. It’s just a matter of time until you get discovered. But by using this satellite link, it’s almost impossible to get discovered.”