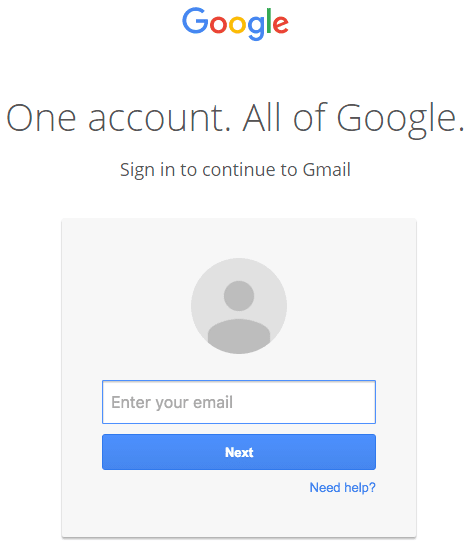
The scam was detected by Wordfence, the maker of a security plugin for WordPress, who said that the victims are targeted via an email to their Gmail account, which may include an attachment or image, and might even come from a contact or company you recognize. When clicked on, it takes users to a well-disguised website that mimics the Gmail login page and asks the user to sign in once more. Once the user enters their password, attackers gain access to their emails and contact list. The problem is, the malicious web link is very well-disguised and even includes “accounts.google.com” in the URL. According to screenshots obtained by Mark Maunder, founder of WordPress security firm Wordfence, the webpage impersonates Google’s official Gmail sign-in page almost identically.
“Once you complete sign-in, your account has been compromised,” Maunder said. In reality, the fake login page that opens up when a user clicks on the image is actually an inline file created using a scheme called Data URI. When users enter their Gmail username and password on the page, the data is sent to the attacker.
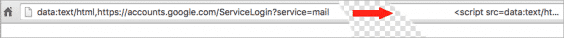
“Once they have access to your account, the attacker also has full access to all your emails including sent and received at this point and may download the whole lot,” he added. “Now that they control your email address, they could also compromise a wide variety of other services that you use by using the password reset mechanism including other email accounts.” The hackers can then spread their virus even further by sending the phishing scam to all your contacts on your behalf. It could get worse, if you use the same login details for other websites or accounts, as the hackers will be able to gain access to these too. Mostly attackers will use a legitimate web address in the hyperlinked text of the email, but once you click on the link it takes you to a malicious website. If you hover your mouse over the link without clicking on it, a small yellow box will appear showing the actual web address the link will take you to. If the link doesn’t match the hyperlinked text, it’s likely malicious. In this instance, when you click on the link or attachment, it will take you to a separate login window. While it might look legitimate, Maunder suggests taking a close look at the URL before entering your password. “Make sure there is nothing before the hostname ‘accounts.google.com’ other than ‘https://’ and the lock symbol. You should also take special note of the green color and lock symbol that appears on the left,” he said. To protect the account and not fall for this trick, ensure that there is nothing in front of the host file name and verify the browser location bar, protocol and hostname. You can also enable two-factor authentication to prevent yourself from being affected. That means a code, sent to your phone via text message, must be entered for completing the login. You can also check your Gmail login history by clicking the “Details” button at the bottom right hand corner of their account pages. If you believe that you may have been affected by this scam already, then you should go ahead and change your password immediately.